Context:
Recently, the US Department of Justice and the FBI blocked a massive Chinese cyber-spying operation known as Volt Typhoon.
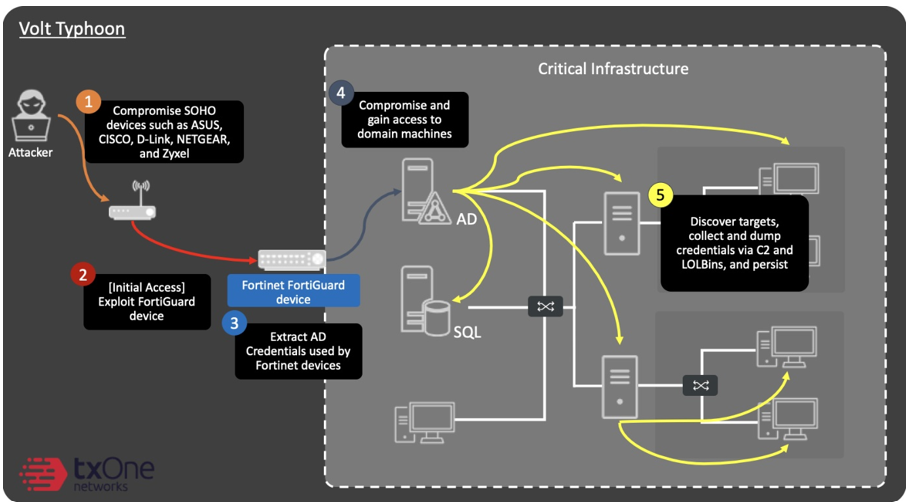
Volt Typhoon:
- It is a Chinese state-sponsored hacking organization that has been active at least since 2021.
- The primary objectives is information collection and counterintelligence.
Target
- It has targeted critical infrastructure organizations across the United States, including Guam.
- Intelligence officials are worried that Volt Typhoon is targeting Western infrastructure, including naval ports, internet service providers, and utilities. Additionally, the use of preinstalled utilities for most victim interactions is rare.
Critical Infrastructure:
- It is a set of systems, networks, and public works that a government considers necessary for its operations and the safety of its population.
Initial Access strategy
- The Volt Typhoon attack pattern starts with getting control over public-facing devices or services.
How it operates:
- Attackers use compromised small office/home office (SOHO) devices to divert communications to and from certain networks.
They use the command line to:
- Collect data, notably information, from local and network machines, and save it in an archive file for exfiltration.
- To ensure continuity, use the stolen valid credentials.
Volt Typhoon was a silent operator who routed traffic through hijacked network equipment, such as residential routers, and carefully removed evidence of intrusions from the target logs.
Stealth Features:
- Volt Typhoon operates with ghost-like tactics, relying on readily available tools and manual commands to stay hidden.
- Secrecy is Volt Typhoon’s game. They avoid detection by using legitimate tools and manual interaction, leaving minimal traces.
Attack Pattern
- Volt Typhoon meticulously gathers information, pilfering credentials from local and network systems in a strategic sequence.
- Volt Typhoon’s attack method systematically retrieves credentials from local and network sources.
Traffic Concealment
- Leaving no digital footprints, Volt Typhoon ghosts through networks, hiding their malicious traffic within compromised home routers.
- Like a chameleon blending into its surroundings, Volt Typhoon hides its attacks by routing traffic through hijacked home routers, erasing their tracks for maximum stealth.
Detection Challenges
- Defenders face an uphill battle, as Volt Typhoon blends in seamlessly with legitimate activity by using pre-installed tools and compromised network equipment.
- Distinguishing friend from foe becomes a near-impossible task for defenders due to Volt Typhoon’s clever mix of tactics, leveraging both built-in utilities and hacked infrastructure.

