Context:
Billionaire entrepreneur Elon Musk’s interview with former US President and Republican Presidential candidate Donald Trump on social media platform X was delayed due to a massive DDoS attack.
About the DDoS attack
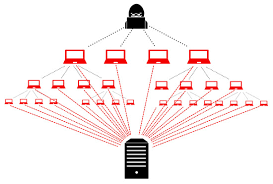
- A ‘Distributed Denial-of-Service (DDoS) Attack’ is a malicious cyberattack in which the attacker floods a server with internet traffic to prevent legitimate users from accessing connected online services and websites.
- The U.S. Cybersecurity & Infrastructure Security Agency (CISA) explains that in a DDoS attack, malicious actors use numerous devices, often compromised through malware, to bombard a target with data packets.
- These packets consume the target’s bandwidth and resources, preventing it from responding to legitimate requests.
DoS vs DDoS
A DoS (denial of services) attack involves a single computer bombarding a system with data requests until the system crashes. In contrast, a DDoS attack aims for the same outcome but utilizes a network of computers, making it significantly more difficult to counter.
- It poses a significant threat to online operations and can lead to downtime, financial losses, and reputational damage for businesses. it is termed a cybercrime.
- In May 2023, a similar incident occurred when Musk hosted Florida Governor Ron DeSantis on X.
- In 2016, for example, major websites like Spotify, Twitter, and Amazon were taken offline for hours due to a DDoS attack.
How do DDoS Attacks operate?
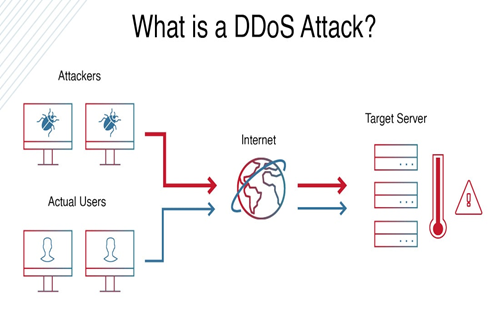
- Botnets: It can be executed through various methods, often involving the use of botnet networks of compromised devices that attackers can deploy to overwhelm a target.
- Smurf Attack: The attacker sends ICMP (internet control message protocol) broadcast packets to multiple hosts using a spoofed source IP address. The hosts respond, flooding the target’s servers and causing a DDoS attack.
- SYN Flood: The attacker sends connection requests to a server but intentionally does not complete them. This causes the server to be overwhelmed by incomplete connections, hindering its ability to handle legitimate requests.
Signs of a DDoS Attack
- Common signs of a DDoS attack include slowed internet speeds, difficulty accessing online services, and intermittent connectivity issues.
- However, these symptoms can also be caused by other factors, so it’s essential to use firewalls and online security systems to verify if a DDoS attack is occurring.
How to Mitigate a DDoS Attack?
- Traditional method: One traditional DDoS mitigation strategy is to reroute malicious traffic to a null route or blackhole, effectively dropping it from the network.
- Rate Limiting: Another approach is rate limiting, which restricts the number of requests a server can accept within a specific time frame.
- For instance, after a recent attack, Elon Musk indicated that X limited the number of listeners for an interview, suggesting that a rate-limiting measure was employed.
- Web Application Firewall (WAF): Placing a WAF between the internet and the origin server allows it to act as a reverse proxy, filtering and mitigating malicious traffic before it reaches the server.
Also Read:
Cabinet Approves Amendment in “Pradhan Mantri JI-VAN Yojana”